共计 2947 个字符,预计需要花费 8 分钟才能阅读完成。
背景
一般我们创建k8s集群后,调用apiserver都是集群vpc内进行访问,如果是是外部网络访问,比如给master配个弹性EIP,博主本地用lens访问这个EIP会报错:
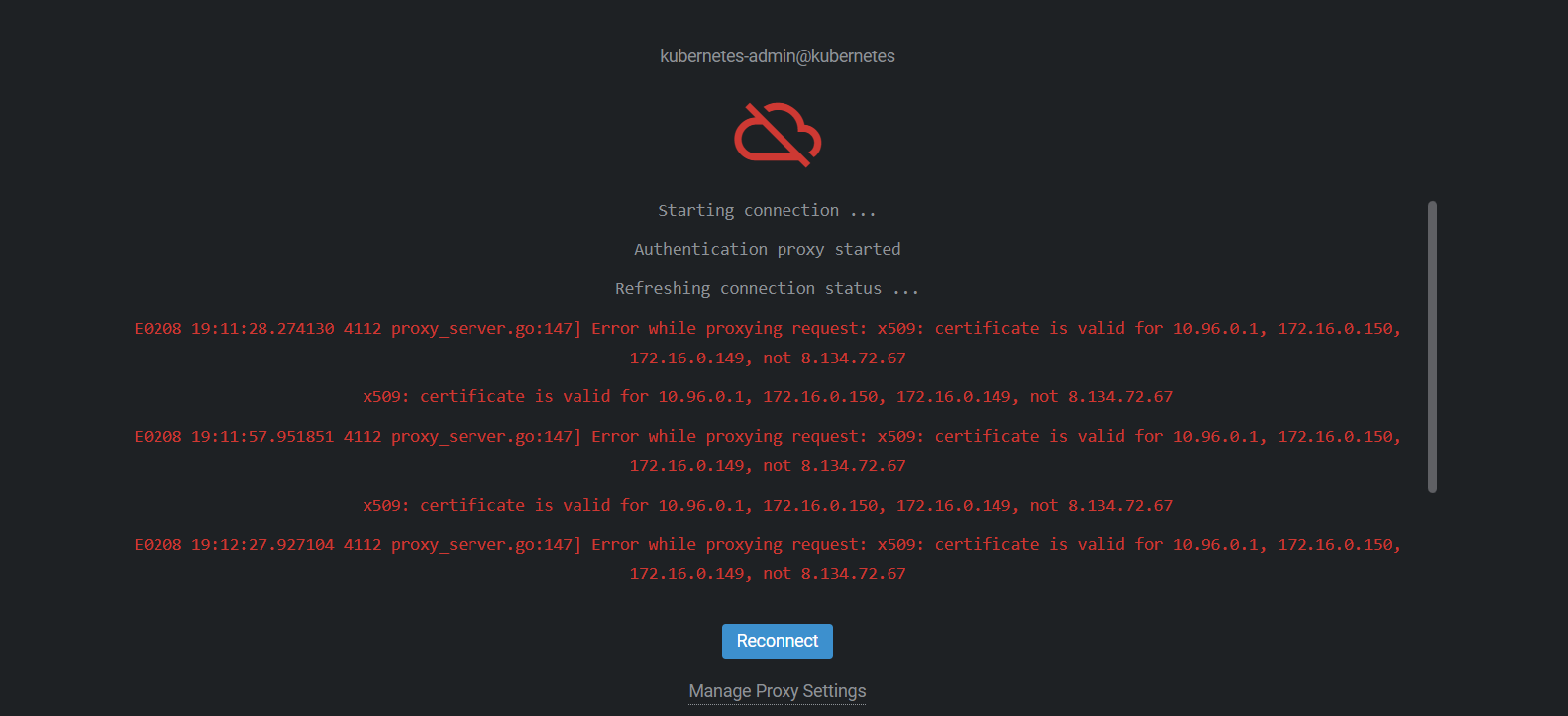
E0208 19:11:28.274130 4112 proxy_server.go:147] Error while proxying request: x509: certificate is valid for 10.96.0.1, 172.16.0.150, 172.16.0.149, not 8.134.72.67kubernetes服务端认证的流程:
client访问apiserver时,apiserver需要校验服务器证书,查看apiserver的证书中认可的ip和域名,与客户端访问apiserver时所采用的ip或域名相比较,判断是否包含。包含则放行,否则报上述错误。
apiserver证书增加访问域名
查看apiserver证书包含的ip和域名
[root@master-0 pki]# openssl x509 -noout -text -in apiserver.crt | grep -C 2 DNS
X509v3 Subject Alternative Name:
DNS:kubernetes, DNS:kubernetes.default, DNS:kubernetes.default.svc, DNS:kubernetes.default.svc.cluster.local, DNS:master-0, IP Address:10.96.0.1, IP Address:172.16.0.149
Signature Algorithm: sha256WithRSAEncryption
71:5c:91:6c:16:c6:c3:87:43:43:31:b5:b8:2b:cb:3e:7a:dc:
从上面可以看到证书的认可的访问域名和地址,如果要增加域名或ip则需要更新证书
备份证书
[root@master-0 ~]# mkdir -p /etc/kubernetes/pki/backup
[root@master-0 ~]# mv /etc/kubernetes/pki/apiserver.{crt,key} /etc/kubernetes/pki/backup/
[root@master-0 ~]# cd /etc/kubernetes/pki/
[root@master-0 pki]# kubectl -n kube-system get configmap kubeadm-config -o jsonpath='{.data.ClusterConfiguration}' > kubeadm.yaml查看此时的kubeadm.yaml
[root@master-0 ~]# cat kubeadm.yaml
apiServer:
extraArgs:
authorization-mode: Node,RBAC
timeoutForControlPlane: 4m0s
apiVersion: kubeadm.k8s.io/v1beta3
certificatesDir: /etc/kubernetes/pki
clusterName: kubernetes
controlPlaneEndpoint: 172.16.0.149:6443
controllerManager: {}
dns: {}
etcd:
local:
dataDir: /var/lib/etcd_pod
imageRepository: k8s.gcr.io
kind: ClusterConfiguration
kubernetesVersion: v1.22.1
networking:
dnsDomain: cluster.local
podSubnet: 10.244.0.0/16
serviceSubnet: 10.96.0.0/12
scheduler: {}
增加外网域名或ip地址
[root@master-0 pki]# cat kubeadm.yaml
apiServer:
extraArgs:
authorization-mode: Node,RBAC
certSANs:
- "k8s.xadocker.cn"
timeoutForControlPlane: 4m0s
apiVersion: kubeadm.k8s.io/v1beta3
certificatesDir: /etc/kubernetes/pki
clusterName: kubernetes
controlPlaneEndpoint: 172.16.0.149:6443
controllerManager: {}
dns: {}
etcd:
local:
dataDir: /var/lib/etcd_pod
imageRepository: k8s.gcr.io
kind: ClusterConfiguration
kubernetesVersion: v1.22.1
networking:
dnsDomain: cluster.local
podSubnet: 10.244.0.0/16
serviceSubnet: 10.96.0.0/12
scheduler: {}
更新证书
[root@master-0 pki]# kubeadm init phase certs apiserver --config kubeadm.yaml
[certs] Generating "apiserver" certificate and key
[certs] apiserver serving cert is signed for DNS names [k8s.xadocker.cn kubernetes kubernetes.default kubernetes.default.svc kubernetes.default.svc.cluster.local master-0] and IPs [10.96.0.1 172.16.0.149]
重建apiserver pod
[root@master-0 pki]# kubectl delete pod kube-apiserver-master-0查看此时apiserver的证书
[root@master-0 pki]# openssl x509 -noout -text -in apiserver.crt | grep -C 2 DNS
X509v3 Subject Alternative Name:
DNS:k8s.xadocker.cn, DNS:kubernetes, DNS:kubernetes.default, DNS:kubernetes.default.svc, DNS:kubernetes.default.svc.cluster.local, DNS:master-0, IP Address:10.96.0.1, IP Address:172.16.0.149
Signature Algorithm: sha256WithRSAEncryption
71:5c:91:6c:16:c6:c3:87:43:43:31:b5:b8:2b:cb:3e:7a:dc:
注意:如果是高可用master的集群,则每个master都要完成上述步骤(备份证书->。。。。->重建apiserver pod)
所有master操作完后即可通过增加的域名来访问apiserver
正文完

 隐私政策
隐私政策 留言板
留言板 金色传说
金色传说 kubernetes
kubernetes terraform
terraform 云生原
云生原 helm
helm 代码编程
代码编程 Java
Java Python
Python Shell
Shell DevOps
DevOps Ansible
Ansible Gitlab
Gitlab Jenkins
Jenkins 运维
运维 老司机
老司机 Linux 杂锦
Linux 杂锦 Nginx
Nginx 数据库
数据库 elasticsearch
elasticsearch 监控
监控 上帝视角
上帝视角 DJI FPV
DJI FPV DJI mini 3 pro
DJI mini 3 pro 关于本站
关于本站